The rapid rise and global adoption of Web3 have brought both significant opportunities and notable risks. Vulnerabilities in widely used dApps and services, along with inconsistent adherence to security best practices, can lead to serious financial and reputational consequences—for both users and projects.
Security ratings offer an objective way to monitor the security posture of Web3 projects, tracking whether it is improving or deteriorating over time. Often backed by in-depth data, these ratings help users assess risk more effectively and make informed decisions, while enabling projects to identify and address potential security weaknesses critical to their long-term success.
The Skynet Score, a real-time rating system from CertiK, was developed to make complex security signals understandable through a single, unified benchmark, thereby enhancing transparency in Web3 security. It offers a clear, data-driven snapshot of a Web3 project’s current health and risk factors, empowering participants globally to make informed decisions and fostering a more trustworthy, secure ecosystem.
Our commitment is to deliver reliable, data-driven, and dynamic security analytics for Web3 projects, coupled with complete transparency regarding our processes and methodologies. By providing users, developers, investors, and platforms with standardized, actionable intelligence from a security-first perspective, the Skynet Score aims to improve transparency and decision-making throughout the Web3 ecosystem.
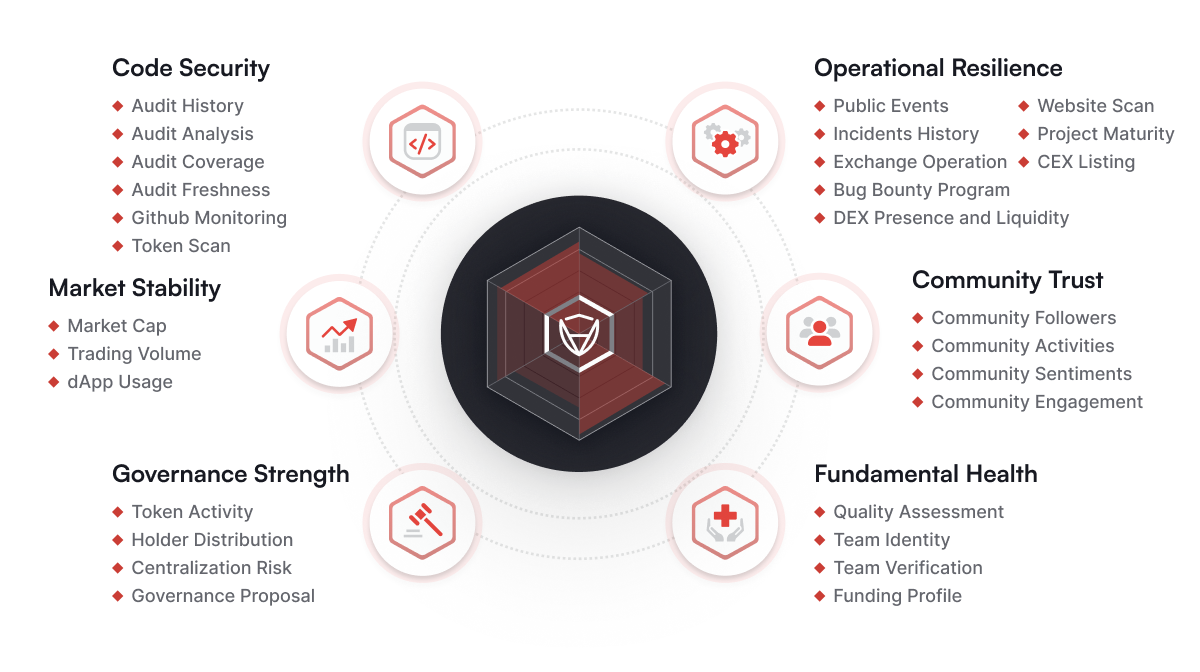
The Skynet Score is a comprehensive rating system built by CertiK’s security researchers to evaluate the overall risk profile of Web3 projects by analyzing key on-chain and off-chain indicators across six core categories:
- Code Security
- Fundamental Health
- Operational Resilience
- Governance Strength
- Market Dynamic
- Community Trust
Although these categories cover a wide range of project attributes, each is analyzed for its direct or indirect implications on the overall security and risk profile of the project. While comprehensive, the Skynet Score prioritizes the assessment of factors contributing to a project's security posture and resilience against threats.
| Core Evaluation Category | Primary Focus Area | How it Ties to Security & Risk |
|---|---|---|
| 1. Code Security | Assessing the security measures and reviews related to a project's source code and smart contract development. | To quantify the inherent security risks within the project's smart contracts and codebase. Identifying vulnerable projects that could be exploited, possibly leading to loss, disruption, or compromised data integrity. |
| 2. Fundamental Health | Evaluating the project's legitimacy, foundational strength, team transparency, and financial backing. | To evaluate underlying reputational risks stemming from the project's structure, team accountability, and financial sustainability, which, if deficient, can indirectly increase susceptibility to insider risks. |
| 3. Operational Resilience | Measuring how well a project’s risk parameters in a live environment, including its maturity, infrastructure, and incident response. | To measure the project's preparedness and ability to defend against, and recover from, operational security threats, including infrastructure attacks, past breaches, and inadequate proactive security. |
| 4. Governance Strength | Analyzing the decentralization of decision-making, token holder distribution, and community involvement in governance. | To ensure that the project is not susceptible to centralized failure points or unilateral decisions detrimental to the community and potentially exploitable for malicious control or manipulation. |
| 5. Market Dynamic | Gauging the project's real-world market traction, financial dynamics, trading activity, and dApp utility. | To identify market behaviors and token-related factors that could indicate heightened security risks, such as abnormal trading patterns suggestive of insider activity prior to exploits. |
| 6. Community Trust | Assessing public engagement, community activity levels, overall sentiment, and direct feedback concerning the project. | To gauge community vigilance and sentiment as an indirect measure of perceived security and trust. A project less transparent and engaged with the community displays lowered transparency and trust. |
The Skynet Score is presented on a scale of 0-100. This numerical score may be accompanied by a letter grade (e.g., AAA, AA, A, BBB, etc.). The score reflects a comprehensive assessment across the multiple dimensions of a Web3 project as detailed in this methodology.
The Skynet Score is designed to correlate with a project's security resilience. While no score can guarantee immunity from security incidents, analysis indicates that projects with consistently lower Skynet Scores may exhibit a statistically higher likelihood of experiencing adverse security events, such as smart contract exploits, operational breaches, or other security-related failures, compared to projects maintaining higher scores. Conversely, higher scores generally reflect more robust security practices and a lower assessed security risk profile.
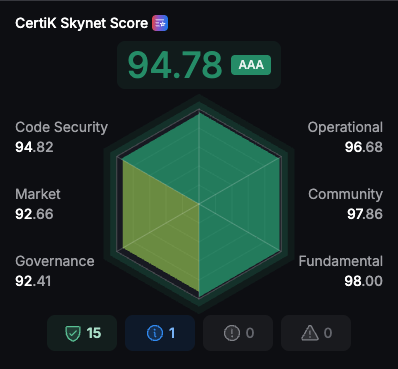
The Skynet Score offers insights into a Web3 project's overall assessed health and security resilience based on this stated methodology. It is designed to be a significant data point in any evaluation process, encouraging users to go deeper into the specific category scores and the underlying indicators for a more granular understanding of a project's particular strengths and areas for potential improvement. The score is a dynamic indicator, reflecting the project's status based on the latest available data.
The Skynet Score is designed to be as objective and unbiased as possible. Most metrics are automated to minimize human influence, ensuring consistency across evaluations. Projects are encouraged to contact the team at [email protected] or via the official Telegram @certikconsult to share feedback or provide missing information that may improve the accuracy of their score.
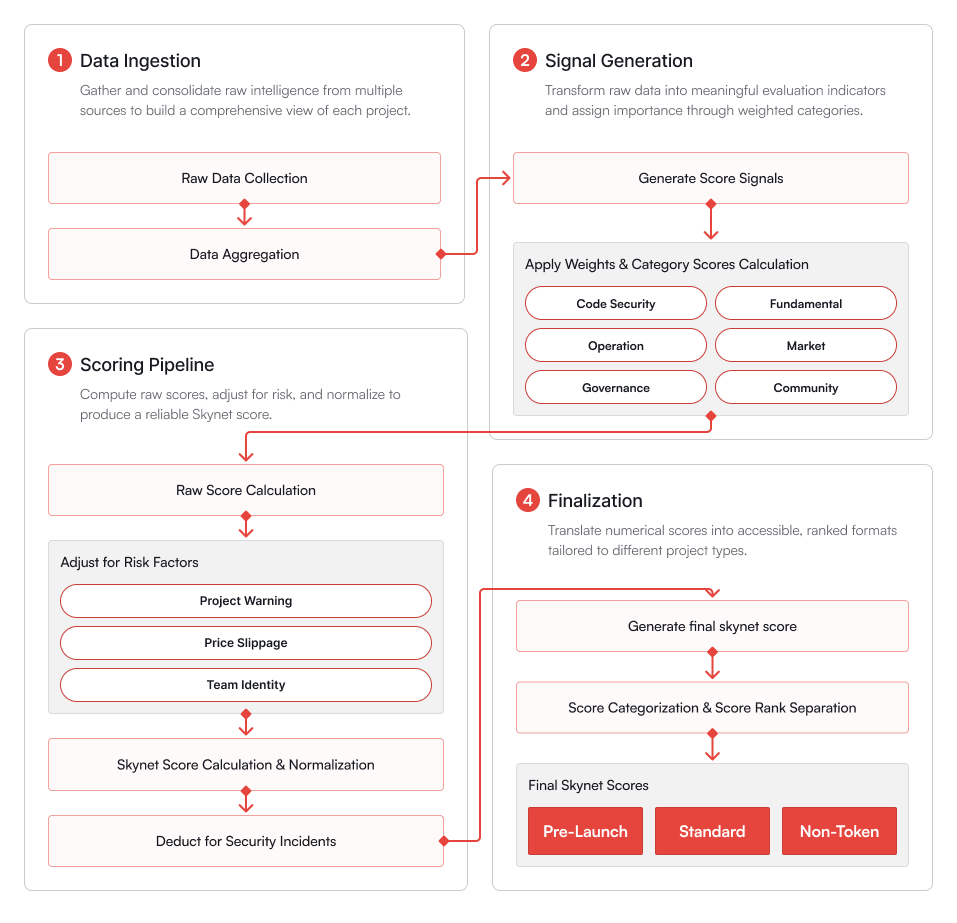
The Skynet Score is a comprehensive security and risk assessment metric designed to provide transparent insights into the trustworthiness of blockchain projects. The calculation workflow follows a structured, multi-stage process:
- Raw Data Collection & Data Aggregation:
Data is sourced from on-chain activity, code repositories, project documentation, community channels, and third-party platforms. - Signal Generation:
Key security and operational signals are extracted from the aggregated data to power the scoring engine. - Apply Weights & Category Score Calculation:
Signals are mapped across six core categories: Code Security, Fundamental, Operation, Market, Governance, and Community, with each category weighted based on its relevance. - Raw Score Calculation:
Weighted scores across categories are combined to produce an initial raw score. - Risk-Based Deductions:
Adjustments are made based on project risks such as price slippage, team anonymity, and project warnings. - Normalization & Incident Adjustments:
The score is normalized for comparability and adjusted further in response to security incidents or vulnerabilities. - Final Score Ratings:
The finalized score is translated into a Skynet Score rating, offering users a simplified security and reliability benchmark. - Categorization & Rank Separation:
Projects are then categorized into Pre-Launch, Standard, or Non-Token profiles based on their current stage and characteristics.
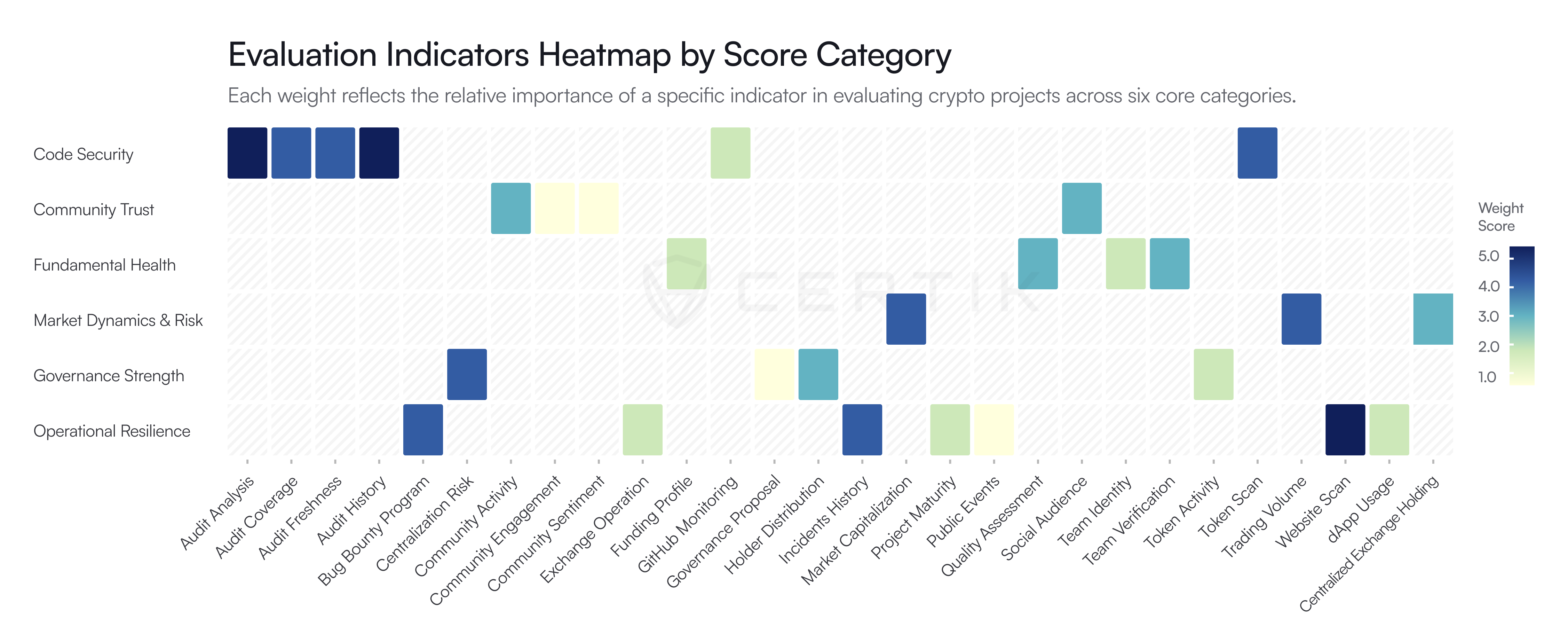
The Skynet Score is derived through a weighted aggregation of numerous indicators across its six core evaluation categories. A foundational principle of this methodology is the significant emphasis placed on security-related factors. Consequently, indicators directly assessing a project’s security, such as code integrity and audit history, carry the highest weight and exert the greatest influence on the overall score. While other, less security-focused variables provide contextual insight and enrich the risk profile, their weighting is calibrated to support the score’s primary objective: to serve as a robust and reliable indicator of a Web3 project’s security posture and readiness against potential threats.
This category serves as the core foundation for CertiK’s proprietary rating system for Web3 projects and is the highest weighted out of all categories. Code Security assesses the steps taken by the project to ensure that its source codes and developments are secured and reviewed via best practices.
Code security audits serve as critical indicators of a Web3 project's commitment to smart contract safety. A robust audit history demonstrates proactive security measures and contributes to reducing potential vulnerabilities.
- Process: For each project listed on Skynet, all publicly available audit reports from established security providers within the ecosystem are systematically aggregated.
- Analysis: This involves comprehensive data collection of published audit reports across industry-leading security firms. Audits are categorized and weighted based on factors such as the audit firms’ reliability, industry standards, and a quantitative analysis of audit frequency per project.
The audit analysis framework evaluates through two key dimensions: (1) a systematic examination of audit report data, where security findings transform into quantifiable metrics through a structured parsing process, and (2) analyzing the project team's responsiveness and remediation efforts. This framework aims to provide layered insights—initial findings can reveal code quality and development rigor, while remediation patterns may demonstrate security commitment and improvement over time.
- Components: The first component involves extracting and categorizing identified security findings, assessing their severity levels, and evaluating the scope of code coverage examined during the audit process. The second component tracks issue resolution rates, which accounts for the inherent risk of unresolved vulnerabilities and architectural centralization risks.
- Weighting: Each finding is weighted according to its potential impact and the complexity of required fixes. When available, formal verification results are used to further enhance the analysis of the audit data.
It is not uncommon for Web3 projects to either lack comprehensive security audits or to refrain from disclosing such audits publicly. In these instances (though this is still a weighting signal for projects with audits), near real-time smart contract security scans are conducted utilizing the project's primary token addresses on-chain.
- Function: This process functions as a supplementary security measure designed to identify potential vulnerabilities that may otherwise go unnoticed.
- Indication: The presence of issues or warnings from these scans may also be indicative of broader lapses in security best practices across the project's associated smart contracts.
Audit coverage analysis measures the proportion of a project's codebase that has undergone professional security review compared to the in-production smart contracts on-chain that users interact with.
- Process: Audited code scope is systematically extracted and parsed from published audit reports, verified on-chain contracts, and official repositories. NLP and code similarity algorithms are then employed to map audited segments to deployed contracts.
- Calculation: The coverage calculation accounts for both directly audited code and verified similar components, expressed as: (Audited SLOC (Source Line Of Code) + Similar Code Components) / Total Project SLOC. This approach prioritizes core logic and aims to detect material discrepancies between audited and production code.
- Significance: Achieving high audit coverage demonstrates security validation by ensuring critical code undergoes professional scrutiny. This metric also helps verify alignment between documented and deployed code, reflecting a project's commitment to operational transparency and security best practices.
Audit freshness assesses whether a project maintains ongoing security reviews of its smart contracts or blockchain code as its codebase evolves through development cycles.
- Evaluation: This metric evaluates both the recency of audits relative to code changes and the frequency of new audits following significant updates.
- Rationale: Since new vulnerabilities can emerge from upgrades or changing threats, a single audit cannot guarantee lasting security. Projects should continuously conduct security audits on core logic after major changes. Consistent audit freshness reflects mature security practices, contributing to minimizing exposure to undetected risks.
A project's public codebase enables essential transparency, allowing for community-driven security through peer review and bug reporting. Active, well-developed codebases indicate a project’s commitment to development.
- Analysis: GitHub metrics – including commit frequency, contributor count, stars, forks, and licensing – are analyzed as key indicators of both technical health and security posture. Regular activity can demonstrate maintained code quality; growing engagement (stars/forks) may reflect community validation, while proper licensing and issue responsiveness can indicate mature development practices. These combined signals provide insights into a project's commitment to secure, collaborative development and ongoing code improvement.
This category is designed to evaluate a project’s legitimacy, transparency, and potential for long-term success. It provides a comprehensive view of a project's foundational strength, focusing on documentation quality, team background, and backers. A strong fundamental health score reflects the credibility of the project and serves as a key risk signal to users, investors, and institutions.
This component focuses on evaluating the availability and completeness of essential project information. A lack of clear, comprehensive, and accessible information can obscure potential risks and hinder due diligence.
- Goal: To assess how well a project presents itself across trusted platforms and public channels, which reflects its commitment to transparency and accessibility.
- Computation: The quality score is computed based on the presence of elements such as a website, whitepaper, Twitter (X) account, Discord server, Telegram channel, LinkedIn page, GitHub repository, and listings on CoinMarketCap, CoinGecko, etc. Each element contributes a specific weight.
Evaluates whether the project has completed a formal team verification process through trusted vendors. Verified team members have more accountability and desire for transparency compared to unverified teams.
- Significance: Team-level verification enhances accountability and strengthens community trust in the team operating the project, potentially reducing the likelihood of unexpected exits that could jeopardize user assets.
- Consideration: A less recent verification certificate may indicate a higher risk, as the team composition or circumstances may have changed over time. It is recommended that projects periodically re-evaluate and renew their team verification to maintain credibility.
Assesses the transparency and verifiability of the founding and existing teams through open-source intelligence methods. Anonymity or lack of verifiable experience in key team members can elevate the risk profile, particularly concerning accountability and the potential for insider threats or project abandonment.
- Methods: This includes background checks, professional experience evaluation, and public presence analysis of disclosed team members.
Trusted institutional investors typically perform a baseline level of independent due diligence on the project prior to funding, which can act as a signal towards a reduced risk profile.
This metric assesses the project’s financial backing through three key dimensions:
- Funding Amount: Total funds raised.
- Funding Round: Tier of the round (e.g., Seed, Series A).
- Funding VC Tier: Based on the reputation of participating investors.
The Operational category reflects how well a project is functioning operationally, across its maturity, sustained development, ecosystem integration, and security responsiveness. It considers tangible signals like exchange listings and liquidity, as well as broader indicators of engagement, infrastructure upkeep, and public presence. By combining both on-chain and off-chain metrics, it offers a clear view of whether a project is actively maintained, trusted by users, and evolving in a healthy, sustainable way.
This signal evaluates the cybersecurity posture of the project’s primary public-facing websites, which often serve as the first point of user interaction and a central hub for critical project resources such as dApp, documentation, smart contract addresses, user dashboards, or token sales.
Assessment Scope:
- The evaluation is based on three core dimensions:
-
Network Security: Identifies exposed network services (e.g., FTP, RDP, VNC, RSYNC) that may be unintentionally accessible over the internet, increasing the risk of unauthorized access or system compromise.
-
Application Security: Evaluates the implementation of fundamental web security practices, including the use of secure protocols, proper certificate management, and key protective headers to guard against common web-based threats.
-
DNS Health: Examines DNS records for missing or ineffective email security policies (SPF, DKIM, DMARC), improper record alignment, and unnecessary exposure of name server details—issues that can lead to spoofing, phishing, or data leakage.
This indicator assesses the project's commitment to proactive vulnerability discovery and remediation through the maintenance of a robust, ongoing bug bounty program.
- Significance: Projects that engage the white-hat community to identify vulnerabilities demonstrate a proactive commitment to security and operational resilience.
- Monitoring: Listings across leading bounty platforms are monitored, and key scoring metrics such as assets in scope, allocated funds, severity classifications, and the most recent update timestamp are incorporated.
Incidents History evaluates a project's past exposure to security breaches, exploits, or other operational failures—and how the team responded. This component serves as a critical retrospective signal of the project's real-world resilience, maturity, and accountability under pressure.
- Evaluation: This signal evaluates the number and severity of past issues, their impact, and any resulting financial losses. How the team responded to these incidents also influences the score. For example, projects demonstrating strong crisis management (e.g., engaging in hacker negotiations, conducting thorough incident analyses in collaboration with security firms, and ultimately mitigating losses or keeping user assets intact) are assessed accordingly.
Evaluates how long the project has been active. Younger projects may inherently carry higher operational risks due to less battle-tested systems and processes, potentially leading to security oversights.
- Basis: Based on token creation date, the age of associated social media accounts (e.g., Twitter), and the inception date of its GitHub repository. Older, well-established projects typically indicate more stable and mature operations.
Tokens with broader CEX and DEX listings, higher liquidity, and greater trading volumes are generally more accessible, actively used, and indicative of stronger operational health. Concentration of tokens on low-tier or poorly secured exchanges can expose tokens and users to higher counterparty and security risks.
- CEX Listing: Evaluates whether the token is listed on major exchanges, factoring in the quality and tier of the exchanges. Visibility on reputable CEXs reflects operational credibility and user accessibility.
- DEX Presence and Liquidity: Evaluates a project's presence and liquidity on decentralized exchanges. It considers both the number of liquidity pools (indicating how widely the token is traded) and the depth of liquidity (reflecting real user interest and market activity).
This subscore evaluates the token’s real-world utility within decentralized applications (dApps). Applications with real adoption and a growing user base have a demonstrated ability to handle real world deployment situations without immediate security concerns.
- Analysis: Beyond in-house analysis, partnerships with leading solutions like DeFiLlama and DappRadar provide comprehensive analysis. Key indicators include:
- On-Chain Transactions: Frequency and volume of dApp interactions.
- Active Wallets: Number of unique addresses interacting with the dApp.
- User Balances and TVL: Distribution and value held across dApps, showing usage depth and stickiness.
This indicator reflects qualitative activity signals that are considered for analysis. Projects with consistent activity show greater commitment to long term sustainability.
- Examples: Mentions, such as token unlocks or CEX listings, on crypto event calendars and sentiment or activity trends in recent media coverage. Such signals can provide insight into a project's visibility, relevance, and overall momentum within the public sphere.
The Governance component of the Skynet Score evaluates the decentralization and effectiveness of a project's decision-making framework and community involvement. A well-structured governance model can foster transparency, inclusivity, and long-term sustainability by encouraging active stakeholder engagement. On the other hand, a highly concentrated holder base and centralized governance structure makes a project vulnerable to manipulation by a small group of insiders.
Centralization risk assesses the security vulnerabilities arising from the concentration of control within the token's smart contract architecture. It specifically scrutinizes the extent to which privileged roles or single points of failure could be exploited to compromise the contract's integrity, manipulate its state, or unilaterally alter its core functions, potentially leading to unauthorized fund drainage, governance hijacking, or operational disruption.
- Assessment: Performed using automated scanning tools, including CertiK's Token Scan and benchmarks from other industry solutions, to detect the presence of privileged functions that may pose security or governance risks.
- Key Elements Analyzed:
- Administrative Access Controls: Functions that allow privileged accounts to alter core contract behavior or parameters.
- Minting/Burning Capabilities: Permissions that enable token supply manipulation, which, if uncontrolled, could impact token economics.
- Pause/Freeze Functionalities: Mechanisms that allow suspension of transfers or contract activity, potentially undermining trust in decentralization.
Holder distribution evaluates the distribution of token supply among holders, with particular emphasis on the concentration of tokens in top addresses. Extreme concentration, especially in externally owned accounts with no clear vesting or multi-sig controls, can present a security risk if those accounts are compromised or act maliciously, potentially leading to market manipulation or governance attacks that destabilize the project.
- Analysis: Projects with broader token ownership are generally considered to be more aligned with the principles of decentralization and community resilience. CertiK's on-chain address labeling infrastructure augments this analysis by attributing wallet ownership where possible, enabling a more precise evaluation of governance-related centralization risks by differentiating between known centralized entities, internal team wallets, and organic user adoption.
Token activity measures the on-chain engagement and liveness of the project's ecosystem, reflecting how actively users and the broader community interact with the protocol. This indicator also assesses patterns in token movements that could signal security risks, such as large, unexplained outflows from team or treasury wallets, sudden high-velocity transfers to centralized exchanges potentially preceding security incidents, or unusual contract interactions indicative of probing or exploitation attempts.
- Evaluation: Conducted using the volume of transactions within specified time intervals and the number of unique wallet addresses interacting with the project, serving as proxies for community engagement and adoption.
This signal evaluates the degree of stakeholder engagement in the project’s governance process. Active and inclusive governance can be essential for decentralized decision-making, long-term sustainability, and alignment between project contributors and the wider community. It reduces the risk of a centralized entity making sole decisions that could impact the integrity of the project.
- Focus: This component focuses on how frequently governance mechanisms are utilized and the quality of community involvement in those processes.
- Key Evaluation Metrics:
- Proposal Frequency: The number of governance proposals submitted over a given timeframe (e.g., monthly, quarterly). A higher frequency of proposals often reflects an engaged and evolving project.
- Approval Rate: The percentage of proposals that successfully pass through community voting. While a high approval rate can indicate consensus, unusually high or low rates may signal governance inefficiencies, voter apathy, or centralization of voting power.
- Participation Quality: This measures the level of community engagement during the voting process, including voting turnout (the proportion of eligible voting power) and contributor diversity (the range of unique wallets or individuals contributing to governance).
- Scoring: Projects that demonstrate consistent proposal activity, balanced approval dynamics, and strong, diverse participation are awarded higher scores in this category, as such characteristics indicate a robust governance system.
The Market component evaluates the project’s real-world traction, on-chain trade activity, and retail investor sentiment. These signals help assess the maturity, visibility, and financial activity surrounding a token once launched. A strong market presence often correlates with higher adoption, increased liquidity, and improved project sustainability. This component aggregates signals from both centralized and decentralized markets and includes measures to reduce the impact of short-term volatility or manipulation.
This measures the overall value of the token based on circulating supply and current price. A higher market cap generally reflects greater adoption, investor confidence, and perceived legitimacy in the ecosystem. It also reduces the likelihood of risk factors such as market manipulations.
- Additional Considerations:
- Market Cap Tracking: Presence on reputable centralized or decentralized exchanges with data sources from platforms like CoinMarketCap and CoinGecko.
- Price Stability: Market resilience during volatile periods. Extreme and idiosyncratic price volatility, especially if uncorrelated with broader market movements, can be an indicator of underlying instability, potential market manipulation, or a loss of confidence possibly linked to perceived or actual security risks.
- Exchange Coverage: Broader availability across exchanges enhances price discovery, user access, and trading confidence. Projects with limited exchange listings or those relying solely on illiquid DEX pairs may be viewed as having limited market reach.
This indicator assesses trading volume across various timeframes to gauge market depth and investor engagement, which can indirectly influence security. Consistently low trading volume may signify heightened risk of price manipulation (e.g., 'pump and dump' schemes) and can create 'exit liquidity' challenges for token holders during security incidents or adverse events, potentially trapping assets or forcing sales at unfavorable prices.
- Analysis:
- 24-Hour and 7-Day Volume: Recent trading volumes are reviewed across major exchanges and normalized by market cap to assess relative liquidity.
- Volume Trends & Moving Averages: Incorporation of moving averages (e.g., 7-day or 30-day) to identify consistent trading behavior and filter out anomalies caused by isolated events or potential wash trading.
- Volume Distribution: The distribution of volume across centralized (CEX) and decentralized (DEX) venues is examined. Excessive reliance on a single exchange, particularly one with a questionable security track record, can introduce liquidity risks and make the project more susceptible to manipulation or issues stemming from that exchange's security posture.
The Exchange Holding indicator provides insight into the concentration and distribution of a project's token holdings across centralized exchanges (CEXs). By aggregating and analyzing the balances of known Proof of Reserve (PoR) wallets maintained by exchanges, this signal offers a transparent view of how much of a token is held by major trading platforms.
- Market Confidence: Large and stable exchange holdings may indicate strong institutional trust and user demand.
- Liquidity Insight: Tokens with substantial holdings on exchanges are typically more accessible for trading, enhancing liquidity and price stability.
- Custodial Risk Monitoring: Understanding how much supply is held in exchange-controlled wallets helps assess potential risk in the event of centralized custody failures.
To derive this indicator, we maintain a curated list of PoR wallet addresses for each major exchange and periodically calculate the token balances held in these wallets. The result is a data-driven indicator of token presence and movement within the centralized trading ecosystem.
The Community component of the Skynet Score captures the presence, activity, sentiment, and engagements surrounding a project across decentralized social channels. A strong and active community can serve as both a signal of legitimacy and a buffer against centralized control or insider risk. This score is composed of both quantitative metrics and tiered sentiment evaluations, sourced from widely used platforms like Twitter/X, Telegram, and Discord, and major news platforms such as CoinDesk, Cointelegraph, Chaincatcher, and many more. In addition, real-time engagement signals from CertiK's own platform—such as user voting, comments, and likes—are integrated to capture direct community sentiment from within the ecosystem itself.
This indicator evaluates the project's social media footprint (audience size, activity, platform diversity) as it pertains to its ability to manage security-related communications and its potential attack surface for social engineering or disinformation campaigns.
- Data Sources: Twitter/X, Discord, and Telegram. Scores are calculated using percentile rankings relative to all listed projects in CertiK's network.
This metric assesses the frequency, transparency, and substance of a project's communications regarding development progress, security practices, and growth milestones.
- Analysis: Each metric is percentile-ranked against all listed projects.
Captures external sentiment toward the project through aggregated news coverage, social media trends, and internal community feedback.
- Data Sources: Leading third-party media platforms as well as user comments and interactions within CertiK's network. Sentiment is analyzed using AI-driven tools, and scores are assigned based on a tiered sentiment model.
Measures direct community engagement through user-generated signals such as ratings, voting, comments, and likes within the CertiK platform.
- Analysis: These inputs reflect real sentiment and trust from active participants in the ecosystem. Bot votes and ratings are detected and filtered to ensure fairness. Scores are determined using a tier-based model that aggregates and weights user feedback across all listed projects.
| Core Evaluation Category | Indicator | Weight | Description |
|---|---|---|---|
| 1. Code Security Assesses security of source code and development practices. | Audit History | High | Aggregated public audit reports from established vendors. |
| Audit Analysis | High | Audit findings, severity, code coverage, and remediation efforts. | |
| Token Scan | High | Near real-time security scans of primary token addresses (if audits lacking). | |
| Audit Coverage | Medium-High | Proportion of codebase reviewed vs. in-production smart contracts. | |
| Audit Freshness | Medium-High | Recency/frequency of audits relative to code changes. | |
| GitHub Monitoring | Medium-Low | GitHub metrics (commits, contributors) for technical health/security. | |
| 2. Fundamental Health Evaluates project legitimacy, team transparency, and foundational strength. | Quality Assessment | Medium | Availability/completeness of website, whitepaper, social presence. |
| Team Verification | Medium | Formal team verification via trusted vendors. | |
| Team Identity | Medium | Transparency/verifiability of founding/existing teams via OSINT. | |
| Funding Profile | Medium-Low | Assessment of financial backing (amount, round, VC tier). | |
| 3. Operational Resilience Reflects real-world functionality, maturity, ecosystem integration, and security responsiveness. | Website Scan | High | Cybersecurity of public website (vulnerability/SSL status). |
| Bug Bounty Program | High | Maintenance of an active bug bounty program. | |
| Incidents History | Medium-High | Track record of security breaches/incidents and team response. | |
| Project Maturity | Medium-Low | Project age (token creation, social accounts, GitHub repo). | |
| Exchange Operation | Medium-Low | CEX listings (quality/tier) and DEX presence/liquidity. | |
| dApp Usage | Medium-Low | Real-world utility within dApps (transactions, active wallets, TVL). | |
| Public Events | Low | Qualitative signals: token unlocks, CEX listings, media sentiment. | |
| 4. Governance Strength Evaluates decentralization, decision-making, and community involvement. | Centralization Risk | Medium-High | Centralized control in smart contract architecture (admin, minting/burning, pause). |
| Holder Distribution | Medium | Token supply distribution, concentration in top addresses. | |
| Token Activity | Medium-Low | On-chain engagement/liveness (transaction volume, unique wallets). | |
| Governance Proposal | Low | Stakeholder engagement (proposal frequency/approval, participation). | |
| 5. Market Dynamic Assesses real-world traction, on-chain trade, and investor sentiment. | Market Capitalization | Medium-High | Overall token value, adoption, investor confidence, price stability, exchange coverage. |
| Trading Volume | Medium-High | Token liquidity/investor interest (recent volume, trends, CEX/DEX). | |
| Centralized Exchange Holding | Medium | Token amount held in CEX’s Proof of Reserve wallets to assess market liquidity and custodial concentration. | |
| 6. Community Trust Captures presence, activity, sentiment, and engagement. | Social Audience | Medium | Audience size/change on major platforms (Twitter/X, Discord, Telegram). |
| Community Activity | Medium | Content output and short-term activity on social platforms. | |
| Community Sentiment | Low | External sentiment (news, social media, internal feedback - AI). | |
| Community Engagement | Low | Direct community engagement on CertiK's platform (ratings, votes, comments). |
The Skynet Score is compiled using data from a wide array of public and proprietary sources. These include, but are not limited to: publicly available audit reports, on-chain blockchain data, code repositories such as GitHub, project websites and whitepapers, social media platforms, crypto news outlets, exchange data feeds, and community interaction platforms. CertiK seeks to use reliable and timely data sources. Data points are processed and analyzed according to the methodologies described under each pillar.
As indicated throughout Section 3 (e.g., "High Weight," "Medium-Low Weight"), each indicator within the six core categories contributes to the overall Skynet Score based on a predefined weighting. These weights reflect CertiK's assessment of each indicator's relative importance to a project's overall security, health, and viability, based on ongoing research and industry expertise. The specific algorithms for score aggregation are proprietary to CertiK.
Each indicator rating is multiplied by its corresponding weight and summed to generate a raw overall score. To produce the final Skynet Score presented in the public-facing product, we apply a normalization process to the raw scores. This ensures the scores follow a desired distribution on a scale up to 100.
Our normalization process is updated daily to account for shifts in the underlying score distributions, except in the case of outlier projects where rating changes are triggered by time-sensitive indicators. As shown in the figure below, the final Skynet Scores achieve a well-distributed range, effectively differentiating security performance and avoiding score clustering.
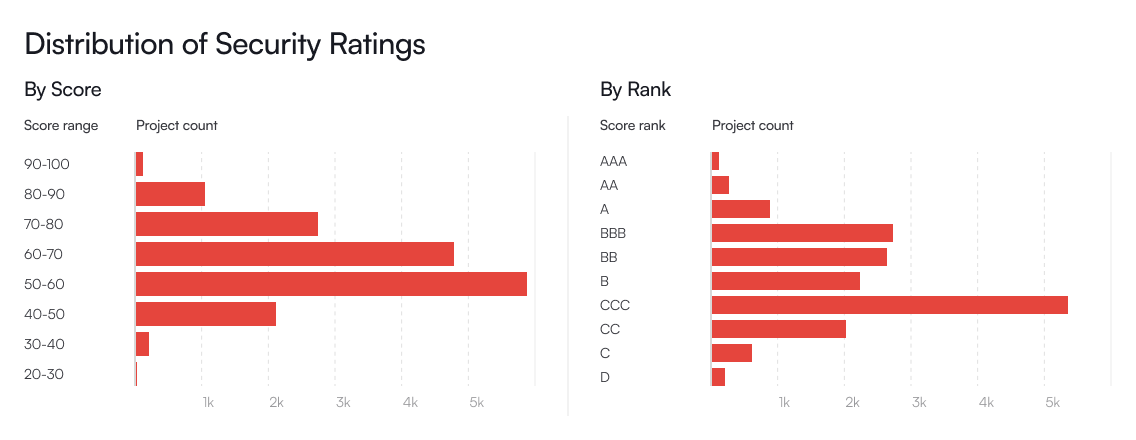
While the Skynet Score offers valuable insights into the security posture of Web3 projects and their trends over time, it has inherent limitations that may occasionally result in ratings that do not fully reflect the true state of a project’s security.
- Due to our outside-in approach, relying solely on externally observable data, we may be unable to detect undisclosed audits or assess internal controls such as private key management. However, projects are encouraged to engage with us under NDA to provide supporting evidence for rating reevaluation where applicable.
- The dynamic nature of Internet and Web3 imposes a fundamental limitation on the accuracy of any process seeking to characterize its current state. As such, the results are probabilistic, not deterministic, and may include occasional false positives or false negatives.
To minimize such errors, we incorporate algorithms, machine learning, and AI into our processes. We are continuously refining our system architecture to enhance the accuracy and timeliness of the Skynet Score.
While the CertiK Skynet Score provides a comprehensive and data-driven assessment, users should be aware of its inherent limitations:
-
External Perspective: The Skynet Score is primarily based on publicly available information, on-chain data, and externally observable factors. It generally cannot assess private internal security practices, undisclosed operational procedures, or the specifics of unverified, closed-source components.
-
Dynamic Nature of Web3: The Web3 space evolves with extreme rapidity. New vulnerabilities, attack vectors, and market dynamics can emerge quickly. The Skynet Score represents an assessment based on available data at a specific point in time and is subject to change.
-
Not Financial or Investment Advice: The Skynet Score is a security and health assessment tool. It is not a financial audit, an endorsement of any project, or investment advice. Users should always conduct their own thorough due diligence (DYOR) before making any financial or participation decisions.
-
Qualitative Aspects: Some indicators, particularly those related to team assessment or community sentiment, involve qualitative analysis that, while systematic and based on defined criteria, may include an element of informed judgment by analysts.
-
No Guarantees: A high Skynet Score indicates strong practices and a lower assessed risk profile based on our methodology, but it is not a guarantee of future success, market performance, or immunity from all possible risks or exploits. Conversely, a low score indicates areas of concern but does not definitively predict failure.
CertiK is a pioneer in blockchain security, leveraging advanced AI technology and expert manual review to secure and monitor blockchain protocols and smart contracts. Founded in 2017 by professors from Yale University and Columbia University, CertiK's mission is to secure the Web3 world. CertiK has established itself as a trusted leader in the industry, having audited and protected substantial value in digital assets for a diverse range of clients globally, from emerging projects to large-scale enterprises.
The Skynet Score is an integral part of CertiK's commitment to this mission. It was developed to bring greater transparency, objective assessment, and data-driven insights to the rapidly expanding and often complex Web3 ecosystem. By providing a comprehensive and continuously updated evaluation of project health and risk, Skynet empowers users, developers, institutions, and the community at large to make more informed decisions and navigate the Web3 space with greater confidence. CertiK believes that security is an ongoing process, not a one-time check. Through Skynet and its comprehensive suite of security solutions, CertiK is dedicated to raising the standards of security and reliability across the blockchain industry, fostering a safer and more trustworthy environment for innovation and adoption.
See the Skynet Score in action and discover all its insights at Skynet.CertiK.com.